Which Topologies Is a Can Able to Use Quizlet
Introduction to Networks ( Version vii.00) – Modules iv – 7: Ethernet Concepts Examination
1. What is the purpose of the OSI physical layer?
- decision-making admission to media
- transmitting $.25 beyond the local media
- performing fault detection on received frames
- exchanging frames betwixt nodes over physical network media
ii. Why are ii strands of fiber used for a single fiber optic connection?
- The two strands permit the data to travel for longer distances without degrading.
- They prevent crosstalk from causing interference on the connection.
- They increase the speed at which the information can travel.
- They allow for full-duplex connectivity.
3. Which feature describes crosstalk?
- the distortion of the network signal from fluorescent lighting
- the distortion of the transmitted messages from signals carried in next wires
- the weakening of the network indicate over long cable lengths
- the loss of wireless signal over excessive distance from the access point
4. Which procedure is used to reduce the effect of crosstalk in copper cables?
- requiring proper grounding connections
- twisting opposing circuit wire pairs together
- wrapping the bundle of wires with metallic shielding
- designing a cable infrastructure to avoid crosstalk interference
- avoiding precipitous bends during installation
5. Match the situation with the advisable use of network media.
half-dozen. A network administrator is measuring the transfer of $.25 across the company backbone for a mission disquisitional fiscal application. The administrator notices that the network throughput appears lower than the bandwidth expected. Which three factors could influence the differences in throughput? (Choose three.)
- the amount of traffic that is currently crossing the network
- the composure of the encapsulation method applied to the data
- the type of traffic that is crossing the network
- the latency that is created by the number of network devices that the information is crossing
- the bandwidth of the WAN connexion to the Internet
- the reliability of the gigabit Ethernet infrastructure of the courage
7. What are two characteristics of fiber-optic cable? (Choose two.)
- It is not affected by EMI or RFI.
- Each pair of cables is wrapped in metallic foil.
- Information technology combines the technique of cancellation, shielding, and twisting to protect information.
- Information technology typically contains four pairs of cobweb-optic wires.
- It is more expensive than UTP cabling is.
viii. What is a primary role of the Physical layer in transmitting information on the network?
- create the signals that correspond the bits in each frame on to the media
- provide concrete addressing to the devices
- determine the path packets take through the network
- control data admission to the media
9. With the use of unshielded twisted-pair copper wire in a network, what causes crosstalk within the cable pairs?
- the magnetic field around the side by side pairs of wire
- the use of braided wire to shield the adjacent wire pairs
- the reflection of the electrical wave back from the far cease of the cablevision
- the standoff caused by two nodes trying to utilize the media simultaneously
x. Refer to the graphic. What blazon of cabling is shown?

- STP
- UTP
- coax
- fiber
11. In addition to the cablevision length, what 2 factors could interfere with the advice carried over UTP cables? (Cull two.)
- crosstalk
- bandwidth
- size of the network
- betoken modulation technique
- electromagnetic interference
12. Refer to the graphic. What blazon of cabling is shown?
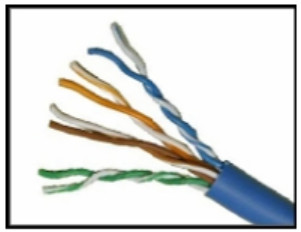
- STP
- UTP
- coax
- fiber
13. Which 2 devices commonly touch on wireless networks? (Cull two.)
- Blu-ray players
- home theaters
- cordless phones
- microwaves
- incandescent lite bulbs
- external hard drives
14. Which two statements describe the services provided by the data link layer? (Choose two.)
- Information technology defines the terminate-to-end commitment addressing scheme.
- It maintains the path betwixt the source and destination devices during the data transmission.
- It manages the access of frames to the network media.
- Information technology provides reliable delivery through link establishment and menstruation command.
- It ensures that application information volition be transmitted according to the prioritization.
- It packages various Layer iii PDUs into a frame format that is compatible with the network interface.
15. What is the function of the CRC value that is found in the FCS field of a frame?
- to verify the integrity of the received frame
- to verify the concrete address in the frame
- to verify the logical accost in the frame
- to compute the checksum header for the data field in the frame
xvi. What is independent in the trailer of a information-link frame?
- logical accost
- physical address
- information
- mistake detection
17. Which statement describes a characteristic of the frame header fields of the data link layer?
- They all include the flow command and logical connexion fields.
- Ethernet frame header fields incorporate Layer 3 source and destination addresses.
- They vary depending on protocols.
- They include information on user applications.
18. A network team is comparison physical WAN topologies for connecting remote sites to a headquarters edifice. Which topology provides loftier availability and connects some, but not all, remote sites?
- mesh
- partial mesh
- hub and spoke
- point-to-point
19. Which ii fields or features does Ethernet examine to determine if a received frame is passed to the data link layer or discarded past the NIC? (Choose two.)
- auto-MDIX
- CEF
- Frame Check Sequence
- minimum frame size
- source MAC address
20. Which media communication blazon does not crave media mediation in the information link layer?
- deterministic
- one-half-duplex
- total-duplex
- controlled access
21. Which statement describes an extended star topology?
- End devices connect to a cardinal intermediate device, which in turn connects to other cardinal intermediate devices.
- End devices are connected together by a double-decker and each charabanc connects to a central intermediate device.
- Each finish arrangement is connected to its respective neighbor via an intermediate device.
- All cease and intermediate devices are connected in a chain to each other.
22. What is a characteristic of the LLC sublayer?
- Information technology provides the logical addressing required that identifies the device.
- Information technology provides delimitation of data according to the concrete signaling requirements of the medium.
- It places data in the frame allowing multiple Layer 3 protocols to utilise the aforementioned network interface and media.
- It defines software processes that provide services to the physical layer.
23. What are 3 ways that media access command is used in networking? (Choose three.)
- Ethernet utilizes CSMA/CD.
- Media access command provides placement of information frames onto the media.
- Contention-based admission is besides known as deterministic.
- 802.11 utilizes CSMA/CD.
- Data link layer protocols ascertain the rules for access to unlike media.
- Networks with controlled access have reduced functioning due to data collisions.
24. During the encapsulation procedure, what occurs at the data link layer for a PC connected to an Ethernet network?
- An IP address is added.
- The logical accost is added.
- The concrete address is added.
- The process port number is added.
25. What three items are contained in an Ethernet header and trailer? (Choose three.)
- source IP address
- source MAC address
- destination IP address
- destination MAC address
- error-checking data
26. What type of advice rule would best depict CSMA/CD?
- access method
- flow control
- bulletin encapsulation
- message encoding
27. Which 3 bones parts are common to all frame types supported by the information link layer? (Choose three.)
- header
- type field
- MTU size
- data
- trailer
- CRC value
28. Which statement is true virtually the CSMA/CD admission method that is used in Ethernet?
- When a device hears a carrier indicate and transmits, a collision cannot occur.
- A jamming betoken causes simply devices that acquired the collision to execute a backoff algorithm.
- All network devices must listen before transmitting.
- Devices involved in a standoff become priority to transmit after the backoff menses.
29. What is the auto-MDIX characteristic on a switch?
- the automatic configuration of an interface for x/100/1000 Mb/s operation
- the automatic configuration of an interface for a directly-through or a crossover Ethernet cable connection
- the automatic configuration of total-duplex operation over a single Ethernet copper or optical cable
- the ability to turn a switch interface on or off appropriately if an active connection is detected
30. Refer to the exhibit. What is the destination MAC address of the Ethernet frame as it leaves the spider web server if the last destination is PC1?
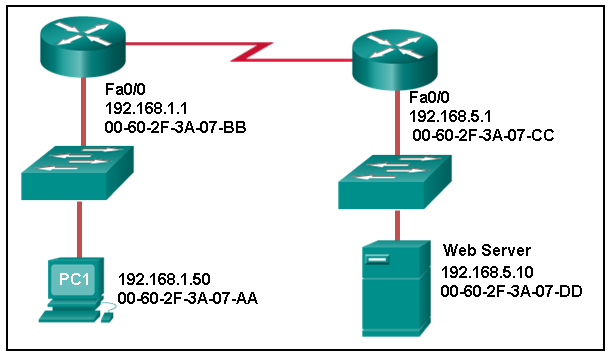
- 00-60-2F-3A-07-AA
- 00-60-2F-3A-07-BB
- 00-lx-2F-3A-07-CC
- 00-60-2F-3A-07-DD
31. A Layer 2 switch is used to switch incoming frames from a 1000BASE-T port to a port connected to a 100Base-T network. Which method of retention buffering would work best for this task?
- port-based buffering
- level 1 enshroud buffering
- shared memory buffering
- fixed configuration buffering
32. What are ii examples of the cutting-through switching method? (Choose two.)
- store-and-forward switching
- fast-forward switching
- CRC switching
- fragment-costless switching
- QOS switching
33. Which frame forwarding method receives the entire frame and performs a CRC bank check to detect errors before forwarding the frame?
- cutting-through switching
- store-and-forwards switching
- fragment-free switching
- fast-frontwards switching
34. What is the purpose of the FCS field in a frame?
- to obtain the MAC address of the sending node
- to verify the logical accost of the sending node
- to compute the CRC header for the data field
- to determine if errors occurred in the transmission and reception
35. Which switching method has the lowest level of latency?
- cut-through
- shop-and-forward
- fragment-costless
- fast-forward
36. A network administrator is connecting 2 mod switches using a direct-through cable. The switches are new and take never been configured. Which three statements are correct about the terminal result of the connection? (Cull three.)
- The link between the switches will work at the fastest speed that is supported by both switches.
- The link between switches will work every bit total-duplex.
- If both switches back up unlike speeds, they will each work at their ain fastest speed.
- The auto-MDIX characteristic will configure the interfaces eliminating the need for a crossover cable.
- The connection volition not exist possible unless the administrator changes the cable to a crossover cable.
- The duplex adequacy has to be manually configured because it cannot be negotiated.
37. Which advantage does the store-and-forward switching method have compared with the cut-through switching method?
- collision detecting
- frame error checking
- faster frame forwarding
- frame forwarding using IPv4 Layer 3 and four data
38. When the store-and-forward method of switching is in use, what part of the Ethernet frame is used to perform an mistake check?
- CRC in the trailer
- source MAC address in the header
- destination MAC address in the header
- protocol type in the header
39. Which switching method uses the CRC value in a frame?
- cut-through
- fast-forrad
- fragment-costless
- store-and-forrad
forty. What are two actions performed by a Cisco switch? (Cull 2.)
- building a routing table that is based on the first IP accost in the frame header
- using the source MAC addresses of frames to build and maintain a MAC address tabular array
- forwarding frames with unknown destination IP addresses to the default gateway
- utilizing the MAC accost tabular array to forward frames via the destination MAC accost
- examining the destination MAC address to add together new entries to the MAC address tabular array
41. Which ii statements describe features or functions of the logical link control sublayer in Ethernet standards? (Cull ii.)
- Logical link control is implemented in software.
- Logical link command is specified in the IEEE 802.three standard.
- The LLC sublayer adds a header and a trailer to the data.
- The data link layer uses LLC to communicate with the upper layers of the protocol suite.
- The LLC sublayer is responsible for the placement and retrieval of frames on and off the media.
42. What is the auto-MDIX feature?
- It enables a device to automatically configure an interface to employ a straight-through or a crossover cablevision.
- It enables a device to automatically configure the duplex settings of a segment.
- It enables a device to automatically configure the speed of its interface.
- It enables a switch to dynamically select the forwarding method.
43. What is ane advantage of using the cutting-through switching method instead of the shop-and-forward switching method?
- has a positive impact on bandwidth by dropping most of the invalid frames
- makes a fast forwarding decision based on the source MAC address of the frame
- has a lower latency advisable for high-performance computing applications
- provides the flexibility to support whatever mix of Ethernet speeds
44. Which is a multicast MAC address?
- FF-FF-FF-FF-FF-FF
- 5C-26-0A-4B-19-3E
- 01-00-5E-00-00-03
- 00-26-0F-4B-00-3E
45. Refer to the showroom. What is wrong with the displayed termination?

- The woven copper braid should not take been removed.
- The incorrect type of connector is being used.
- The untwisted length of each wire is too long.
- The wires are too thick for the connector that is used.
46. Refer to the exhibit. The PC is connected to the console port of the switch. All the other connections are made through FastEthernet links. Which types of UTP cables can be used to connect the devices?
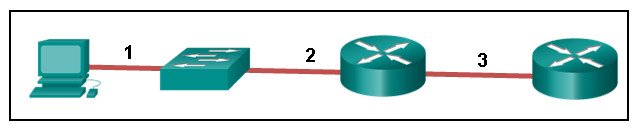
- 1 – rollover, 2 – crossover, 3 – straight-through
- 1 – rollover, ii – direct-through, iii – crossover
- 1 – crossover, two – straight-through, 3 – rollover
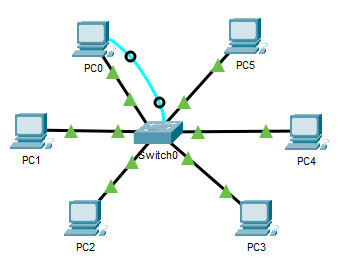
- 1 – crossover, 2 – rollover, 3 – directly-through
47. Open the PT Action. Perform the tasks in the activity instructions and then answer the question.
[sociallocker id="54558″]
[/sociallocker]
Which port does Switch0 use to send frames to the host with the IPv4 address 10.1.1.5?
- Fa0/ane
- Fa0/5
- Fa0/9
- Fa0/11
48. What does the term "attenuation" mean in data communication?
- loss of bespeak strength as distance increases
- time for a indicate to attain its destination
- leakage of signals from i cablevision pair to some other
- strengthening of a signal by a networking device
49. What makes fiber preferable to copper cabling for interconnecting buildings? (Choose iii.)
- greater distances per cablevision run
- lower installation toll
- limited susceptibility to EMI/RFI
- durable connections
- greater bandwidth potential
- hands terminated
50. What OSI concrete layer term describes the process by which 1 wave modifies another wave?
- modulation
- IEEE
- Environmental impact assessment/TIA
- air
51. What OSI physical layer term describes the capacity at which a medium tin can deport data?
- bandwidth
- IEEE
- EIA/TIA
- air
52. What OSI physical layer term describes the capacity at which a medium can carry data?
- bandwidth
- throughput
- latency
- goodput
53. What OSI physical layer term describes the measure of the transfer of bits across a medium over a given flow of time?
- throughput
- bandwidth
- latency
- goodput
54. What OSI physical layer term describes the amount of fourth dimension, including delays, for data to travel from one point to another?
- latency
- bandwidth
- throughput
- goodput
55. What OSI physical layer term describes the amount of time, including delays, for information to travel from one bespeak to another?
- latency
- fiber-optic cablevision
- air
- copper cablevision
56. What OSI physical layer term describes the mensurate of usable data transferred over a given catamenia of fourth dimension?
- goodput
- fiber-optic cable
- air
- copper cablevision
57. What OSI physical layer term describes the physical medium which uses electric pulses?
- copper cable
- fiber-optic cable
- air
- goodput
58. What OSI physical layer term describes the physical medium that uses the propagation of low-cal?
- fiber-optic cable
- goodput
- latency
- throughput
59. What OSI physical layer term describes the physical medium for microwave transmissions?
- air
- goodput
- latency
- throughput
60. Which two functions are performed at the MAC sublayer of the OSI data link layer? (Choose two.)
Select 2 of the correct answers in ruby font
- Enables IPv4 and IPv6 to utilize the same network interface and media
- Adds Layer 2 control information to network protocol data.
- Integrates various physical technologies.
- Communicates between the networking software at the upper layers and the device hardware at the lower layers.
- Provides synchronization betwixt source and target nodes.
- Places information in the frame that identifies which network layer protocol is existence used for the frame.
- Controls the NIC responsible for sending and receiving information on the concrete medium.
- Implements a trailer to detect transmission errors.
- Provides a mechanism to allow multiple devices to communicate over a shared medium.
61. Which ii functions are performed at the LLC sublayer of the OSI data link layer? (Cull two.)
- Enables IPv4 and IPv6 to utilise the same network interface and media.
- Places information in the frame that identifies which network layer protocol is being used for the frame.
- Integrates various physical technologies.
- Implements a process to circumscribe fields within a Layer ii frame.
- Controls the NIC responsible for sending and receiving data on the physical medium.
64. Which two functions are performed at the LLC sublayer of the OSI data link layer? (Choose two.)
- Adds Layer two command information to network protocol data.
- Places information in the frame that identifies which network layer protocol is being used for the frame.
- Performs data encapsulation.
- Controls the NIC responsible for sending and receiving information on the physical medium.
- Integrates diverse concrete technologies.
66. Which two functions are performed at the LLC sublayer of the OSI data link layer? (Cull two.)
- Adds Layer 2 control information to network protocol information.
- Enables IPv4 and IPv6 to utilise the same network interface and media.
- Provides data link layer addressing.
- Implements a trailer to discover transmission errors.
- Provides synchronization between source and target nodes.
68. Which two functions are performed at the LLC sublayer of the OSI information link layer? (Choose two.)
- Enables IPv4 and IPv6 to utilise the same network interface and media.
- Adds Layer 2 control information to network protocol data.
- Integrates diverse physical technologies.
- Implements a trailer to notice transmission errors.
- Provides synchronization betwixt source and target nodes.
70. What activity will occur if a switch receives a frame and does have the source MAC address in the MAC tabular array?
- The switch refreshes the timer on that entry.
- The switch shares the MAC accost table entry with any connected switches.
- The switch does not forward the frame.
- The switch sends the frame to a connected router because the destination MAC address is not local.
71. What activeness will occur if a switch receives a frame with the destination MAC address FF:FF:FF:FF:FF:FF?
- The switch forrad it out all ports except the ingress port.
- The switch shares the MAC address tabular array entry with any connected switches.
- The switch does not forward the frame.
- The switch sends the frame to a connected router because the destination MAC address is not local.
72. What action will occur if a host receives a frame with a destination MAC address it does not recognize?
- The host will discard the frame.
- The host sends the frame to the switch to update the MAC address table.
- The host frontward the frame to the router.
- The host forwards the frame to all other hosts.
73. What action will occur if a switch receives a frame with the destination MAC accost 01:00:5E:00:00:D9?
- The switch forward it out all ports except the ingress port.
- The switch does not forward the frame.
- The switch sends the frame to a continued router considering the destination MAC address is non local.
- The switch shares the MAC address tabular array entry with any connected switches.
74. What activeness will occur if a host receives a frame with a destination MAC address of FF:FF:FF:FF:FF:FF?
- The host will process the frame.
- The host forwards the frame to the router.
- The host sends the frame to the switch to update the MAC accost table.
- The host forwards the frame to all other hosts.
75. What activeness will occur if a switch receives a frame and does have the source MAC address in the MAC table?
- The switch refreshes the timer on that entry.
- The switch adds it to its MAC accost table associated with the port number.
- The switch forwards the frame to the associated port.
- The switch sends the frame to a connected router because the destination MAC accost is not local.
76. What action volition occur if a host receives a frame with a destination MAC address of FF:FF:FF:FF:FF:FF?
- The host will procedure the frame.
- The host returns the frame to the switch.
- The host replies to the switch with its own IP address.
- The host forwards the frame to all other hosts.
77. What activeness will occur if a switch receives a frame and does take the source MAC address in the MAC table?
- The switch refreshes the timer on that entry.
- The switch shares the MAC address table entry with whatever connected switches.
- The switch does not frontward the frame.
- The switch adds it to its MAC address table associated with the port number.
78. What action will occur if a host receives a frame with a destination MAC accost it does not recognize?
- The host will discard the frame.
- The host replies to the switch with its ain IP address.
- The host forwards the frame to all other hosts.
- The host returns the frame to the switch.
79. What action will occur if a switch receives a frame with the destination MAC address FF:FF:FF:FF:FF:FF?
- The switch forwards it out all ports except the ingress port.
- The switch refreshes the timer on that entry.
- The switch does not forward the frame.
- The switch sends the frame to a connected router because the destination MAC address is not local.
eighty. Which blazon of UTP cable is used to connect a PC to a switch port?
- panel
- rollover
- crossover
- directly-through
burgoonevered1950.blogspot.com
Source: https://itexamanswers.net/ccna-1-v7-modules-4-7-ethernet-concepts-exam-answers.html
0 Response to "Which Topologies Is a Can Able to Use Quizlet"
Post a Comment